How to work with the scan report
- Category : Tips and Tricks
- Posted on : Oct 19, 2020
- Views : 2,013
- By : HostSEO

The threat of hacking is a very serious issue. Thatâ$™s why itâ$™s important to pay attention to the security of your cPanel account.
Our Shared Hosting servers have an effective firewall system along with a set of other security measures. However, cPanel account protection also depends on you. By scanning your hosting space for viruses, trojans, malware, and other threats, you ensure its safety.
To locate any malicious software in your cPanel, use the built-in cPanel Virus Scanner or contact our Support Team. We will perform on-demand scanning of your hosting account to ensure it is clean and secure. A detailed report will be provided so you can examine it.
How to locate your scan report
Once the scanning process is complete, a report is uploaded automatically to your cPanel account. To locate it, follow the steps below:
1. Log in to your cPanel.
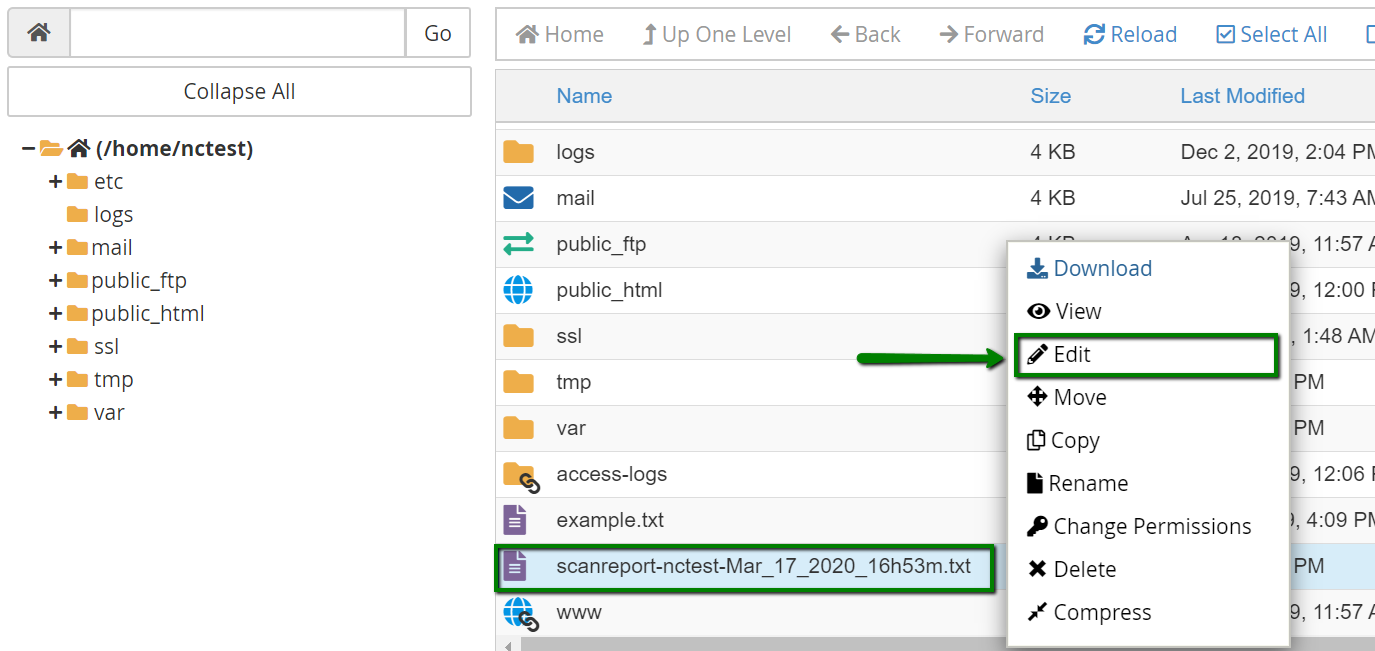
2. Navigate to the Files section >> File Manager:

Usually, its name contains your cPanel username and the date when the file was generated, e.g., scanreport-nctest-Mar_17_2020_16h_53m.txt.
4. Locate the file, right-click >> choose the Edit option.
----------- SCAN REPORT ----------- TimeStamp: Wed, 26 Feb 2020 01:31:39 -0500 (/usr/sbin/cxs --background --nobayes --clamdsock /var/clamd --dbreport --defapache nobody --doptions Mv --exploitscan --nofallback --filemax 10000 --noforce --html --ignore /etc/cxs/cxs.ignore.manual --options mMOLfSGchexdnwZDRru --qoptions Mv --report /home/cPanel_username/scan_report_Feb-26-2020 --sizemax 1000000 --ssl --summary --sversionscan --timemax 30 --unofficial --user cPanel_username --virusscan --xtra /etc/cxs/cxs.xtra.manual) Scanning /home/cPanel_username: '/home/cPanel_username/.bcwfgi.php' # ClamAV detected virus = [YARA.php_malware_hexinject.UNOFFICIAL] '/home/cPanel_username/old/wp-admin/cfgs.php' # Known exploit = [Fingerprint Match] [PHP Exploit] '/home/cPanel_username/old/wp-admin/images/align-lefts.png' # Suspicious image file (hidden script file) '/home/cPanel_username/public_html/assets/asset/js/plugins/editors/codemirror/mode/clike/index.html' # Suspicious file type [application/x-c] '/home/cPanel_username/public_html/assets/asset/js/plugins/uploaders/plupload/files/Moxie.xap' # (compressed file: Moxie.dll [depth: 1]) MS Windows Binary/Executable [application/x-winexec] '/home/cPanel_username/public_html/vendor/laravel/framework/src/Illuminate/Filesystem/Filesystem.php' # Regular expression match = [symlink\s*\(] '/home/cPanel_username/example.com/wp-content/plugins/contact-form-7/wp-contact-form-7.php' # Script version check [OLD] [Contact Form 7 v5.0.5 < v5.1.3] '/home/cPanel_username/example.com/wp-content/themes/weddingvero/auto-install/uploads/espresso/tickets' # World writeable directory ----------- SCAN SUMMARY ----------- Scanned directories: 8221 Scanned files: 77818 Ignored items: 217 Suspicious matches: 893 Viruses found: 743 Fingerprint matches: 85 Data scanned: 5245.76 MB Scan time/item: 0.013 sec Scan time: 1149.580 sec
- path to the directory or file (e.g. '/home/cPanel_username/public_html/vendor/laravel/framework/src/Illuminate/Filesystem/Filesystem.php') ;
- scan result (e.g. # Regular expression match = [symlink\s*\(]).
Taking into account the scan result, you will need to perform certain actions to keep your account secure. Most cases are described in the table below:
NOTE 1: Make sure to create a backup of your cPanel before making any changes.
| Result | Description | Action to take |
|---|---|---|
| # ClamAV detected virus | Antivirus software has found a potentially dangerous file with malware. | Remove a file. |
| # Suspicious file type [application/x-c] # MS Windows Binary/Executable [application/x-winexec] # (compressed file: Moxie.dll [depth: 1]) MS Windows # Binary/Executable [application/x-winexec] # MS-DOS Binary/Executable [application/x-dosexec] | Antivirus software has found Windows binary or executable files. Such files cannot be executed on a Linux-based OS. You would not normally expect to find one within a cPanel account . You can discover a Trojan file among them. | Remove a file. |
| # Linux Binary/Executable [application/x-sharedlib] | Antivirus software has found Linux binary or executable files. Such files can be executed on a Linux-based OS. Still, you would not normally expect to find one within a cPanel account. If a Linux binary or executable file is located in a cPanel account, it is most likely an exploit that remains hidden. | Remove a file. |
| # Known exploit = [Fingerprint Match] | Antivirus software considers a file as an exploit. An exploit can be a program, a piece of code, or even just a string of characters. It takes advantage of a program. Then, this program acts in an unexpected way, which results in undesirable behavior. Also, exploits are maliciously used to gain unauthorized access. | Unless you know the purpose of this file, remove it from your cPanel. If it is related to installed software and you need it, either clean it or upload again from a trusted source. PLEASE NOTE: It is strongly encouraged to use content only from the official source. |
| # Symlink to | The file is a symbolic link. It consists of a special type of file that serves as a reference to another file or directory. Some default files require symlinks for the proper work of cPanel services: '/home/cPanel_username/.cagefs/opt/alt/phpXX/link/conf' '/home/cPanel_username/access-logs' '/home/cPanel_username/.cagefs/tmp/mysql.sock' Â But the custom symlinks (e.g. a symlink to files outside of your cPanel account) may cause serious security breaches. | Pay attention to the custom symlinks. Such files should be removed from your account. Symlinks to default cPanel files can be ignored. |
| # Socket | A socket is typically used to transfer data between two separate processes. You would not expect to normally find one within a cPanel account. | Unless you know the purpose of this file or it is related to the software installed from the trusted source, remove it from your cPanel. |
| # Regular expression match = [symlink\s*\(] | A file contains 'symlink(s)' expression as a comment or variable. | It is a false-positive. The file can be ignored. |
| # Regular expression match = [\n(?!\s*(//|\#|\*)).*/etc/passwd] | A file contains '/etc/passwd' expression as a comment or variable. | It is a false-positive. The file can be ignored. |
| # Regular expression match = [\n(?!\s*(//|\#|\*)).*\.ssh/] | A file contains '/.ssh' expression as a comment or variable. Such files are potentially harmful to your account as they allow remote access using SSH keys. | Unless you know the purpose of this file or it is related to the software installed from the trusted source, remove it from your cPanel. |
| # Universal decode regex match | A file contains some string encoded with a common encoder, e.g. base64. They are often used to hide malicious code. | Unless you know the purpose of this file or it is related to the software installed from the trusted source, remove it from your cPanel. |
| # Script version check [OLD] | The installation, plugin or theme version is outdated. Software updates are important because they check for the bugs and vulnerabilities found in the previous versions. A â$˜holeâ$™ in one can affect your entire installation as well as your cPanel account. | Ensure that your installations are up to date. |
| # World writable directory | Permissions for a directory are set to 777. It is recommended to have default permissions assigned to website files and folders. They are 644 for files and 755 for folders. However, it is safe to have permissions set to 777 for default cPanel folders: /home/cPanel_user/.cagefs/var/cache /home/cPanel_user/.cagefs/var/php /home/cPanel_user/.cagefs/var/run | Update permissions for the indicated directory. |
| # Scan Timeout (30 seconds) while processing | The scan process has been interrupted. | You can put in a request to our Support Team to scan it additionally. |
Categories
- cPanel Question 47
- cPanel Software Management 29
- cPanel Tutorials 13
- Development 29
- Domain 13
- General 19
- Linux Helpline (Easy Guide) 156
- Marketing 47
- MySQL Question 13
- News 2
- PHP Configuration 14
- SEO 4
- SEO 42
- Server Administration 84
- SSL Installation 54
- Tips and Tricks 24
- VPS 3
- Web Hosting 44
- Website Security 22
- WHM questions 13
- WordPress 148
Subscribe Now
10,000 successful online businessmen like to have our content directly delivered to their inbox. Subscribe to our newsletter!Archive Calendar
| Sat | Sun | Mon | Tue | Wed | Thu | Fri |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | ||||||
Recent Articles
-

Posted on : Sep 17
-

Posted on : Sep 10
-

Posted on : Aug 04
-

Posted on : Apr 01
Tags
- ts
- myisam
- vpn
- sql
- process
- kill
- tweak
- server load
- attack
- ddos mitigation
- Knowledge
- layer 7
- ddos
- webmail
- DMARC
- Development
- nginx
- seo vpn
- Hosting Security
- wireguard
- innodb
- exim
- smtp relay
- smtp
- VPS Hosting
- cpulimit
- Plesk
- Comparison
- cpu
- encryption
- WHM
- xampp
- sysstat
- optimize
- cheap vpn
- php-fpm
- mariadb
- apache
- Small Business
- Error
- Networking
- VPS
- SSD Hosting
- Link Building
- centos
- DNS
- optimization
- ubuntu