RUNNING A VPN SERVER ON YOUR VPS – EVERYTHING YOU NEED TO KNOW
- Category : Server Administration
- Posted on : Apr 27, 2018
- Views : 2,928
- By : Marcus J.

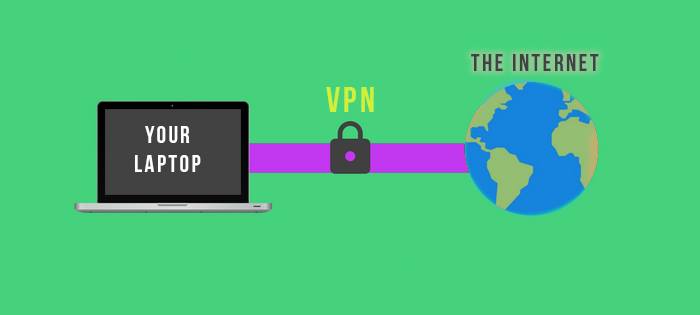
A VPN, or Virtual Private Network, is a service that creates an encrypted tunnel between the location of your computer and a remote server.
All of your Internet traffic is routed through this tunnel, effectively masking your real location since your computer will seem to have the IP address of the VPN server.
In addition, all traffic is encrypted so your data remains safe at all times, even if intercepted by a hacker or your network administrator.
WHY DO YOU NEED A VPN?
The two main benefits of a VPN, anonymity and encryption, have made these services hugely popular. In the modern world, most aspects of our lives are transmitted in one way or another over the Internet.
Every single action that you perform online, like visiting a site or clicking on a photo, is recorded and traced back to your IP address. If you are concerned about your online privacy, using a VPN has become almost mandatory.
Anonymous browsing doesn’t only protect your privacy, but also provides a number of other benefits. Virtual private networks have been used for a long time in countries like China, in order to bypass censorship and Internet access restrictions.
They also allow users to view live streams from all around the world or elude the strict network rules of university access points.
Since the VPN tunnel is always encrypted, you no longer have to worry about using unsecured networks. You can connect to any public WiFi hotspot and do online banking for example, without any risks.
VPN ALTERNATIVES
If you need a VPN, there are three main options: using a free service, a paid one or setting up your own VPN server.
Free services are a bad idea because they are not really secure and have serious limitations, we have already detailed why you should avoid them in a previous article.
Paid VPNs are more reliable but even these are not fully secure and there have been cases when the providers were forced to disclose client data to investigators.
In addition, a monthly VPN subscription is usually more expensive that the cost of setting up your own server. Today, you can provision a VPS (Virtual Private Server) for a really low price and configure it as a VPN in order to hide and secure your Internet traffic. While setting up a VPN is not an easy task, we will guide you through all the steps in this article.
PREREQUISITES
There are several applications that can be used to install a VPN server. In this article, we will use OpenVPN, which provides a very flexible solution.
OpenVPN can be installed on various operating systems, from Windows to Linux or MacOS. It has very low system requirements, so the Host SEO has enough resources to run it effectively. Your server must have a dedicated static IP address.
We will use a CentOS 7.6 VPS with 2 CPU cores and 2 GB RAM but you can go even lower if you want. Before the installation, run a general system update in order to make sure that all packages are upgraded to their latest version.
GETTING YOUR VPS SERVER
Make sure you have a VPS you can run your VPN service on. You can get the best service quality for the lowest price point by getting one of our Host SEO servers.
INSTALLING OPENVPN
The installation process is pretty straightforward. Since OpenVPN is not available from the standard CentOS repositories, the first step is to install EPEL and refresh the list of available packages:
yum install epel-release yum update |
You can now install OpenVPN:
1 | yum install openvpn |
We will also install EasyRSA, a tool that simplifies the setup of an internal certificate authority (CA) on the server and SSL key generation. The package is also available in the EPEL repository and can be easily installed with yum:
1 | yum install easy-rsa |
CONFIGURING OPENVPN
Open VPN has many configuration options, which can be quite complex. Fortunately, a sample configuration file is provided, with comments that explain the functions of each line. Copy it to the default configuration folder and use it as a basis for your own settings file:
1 | cp /usr/share/doc/openvpn-2.4.6/sample/sample-config-files/server.conf /etc/openvpn |
Open the file with your favorite text editor; we will use vim in this example. Since vim’s default color scheme makes comments difficult to read, you can switch to a different one (with a command like :colorscheme desert):
1 | vim /etc/openvpn/server.conf |
Start by changing the default port and protocol to 443 tcp:
port 443 proto tcp |
Next, you have to modify the location of the certificates that will be used by the server:
ca /etc/openvpn/easy-rsa/pki/ca.crt cert /etc/openvpn/easy-rsa/pki/issued/server.crt key /etc/openvpn/easy-rsa/pki/private/server.key dh /etc/openvpn/easy-rsa/pki/dh.pem |
The next two lines that have to be uncommented are:
topology subnet server 10.8.0.0 255.255.255.0 |
These will create a subnetwork that allocates addresses to client machines. The server will use the first address in the subnet (10.8.0.1), while the first client will be assigned the IP 10.8.0.2.
The most important line that must be uncommented is this one:
1 | push "redirect-gateway def1 bypass-dhcp" |
It basically instructs client machines to redirect all their traffic through the VPN, instead of their local gateway. Since using this route will ignore the local network’s DNS servers, new ones have to be defined. In this example, we will use the most popular public DNS servers, provided by Google and Cloudflare:
push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 1.1.1.1" |
In order to improve security and follow official OpenVPN guidelines, enable TLS authentication. Comment the line that begins with tls-auth and define an encryption key that you’ll generate with the name of your choice (mykey.tls in this example):
;tls-auth ta.key 0 tls-crypt mykey.tls |
Adding this line will harden security checks even further:
1 | remote-cert-eku "TLS Web Client Authentication" |
You can also enable compression by uncommenting these two options:
compress lz4-v2 push "compress lz4-v2" |
Finally, configure OpenVPN to run with the user and group nobody, so the service doesn’t have any privileges after it starts. The lines that have to be uncommented are:
user nobody group nobody |
The last line of the file also has to be changed, because this option is not compatible with the TCP protocol:
1 | explicit-exit-notify 0 |
You now have a solid basic configuration in place, so save the file and exit. Since all directives are very well documented in the file, you can tweak other parameters if you want.
Don’t forget to generate the static encryption key by executing this command:
1 | openvpn --genkey --secret /etc/openvpn/mykey.tls |
GENERATE SSL KEYS AND CERTIFICATES
While keys and certificates can be generated in several ways, the scripts installed by EasyRSA make this task very simple.
Create a folder in order to store the keys and certificates that will be generated:
1 | mkdir -p /etc/openvpn/easy-rsa |
Copy the EasyRSA scripts from their initial location to this folder:
1 | cp -r /usr/share/easy-rsa/3.0/* /etc/openvpn/easy-rsa |
Navigate to the configuration folder and run the scripts in order to initialize a new PKI and build a certificate authority (CA):
cd /etc/openvpn/easy-rsa ./easyrsa init-pki ./easyrsa build-ca |
In order to build the CA, you have to enter a PEM pass phrase as well as a Common Name (CN) for your server, or just press Enter for the default value. Make sure that you remember the PEM password, since you will need it later.
The next step is to generate the keys and certificates of the actual OpenVPN server, in this example we will use “server” as the filename. The PEM password is required by the signing request script:
./easyrsa gen-req server nopass ./easyrsa sign-req server server |
The DH parameters used during the TLS handshake with clients are generated by the following command, which takes some time to finish:
1 | ./easyrsa gen-dh |
Every client also needs a certificate in order to connect to the server. It is very important to keep this certificate safe and not share it with others, in order to avoid a massive security risk. If you want to allow other people to use your OpenVPN server, generate a separate certificate for them using the same procedure.
In this example, we will generate a key and certificate for client1, the PEM password is needed again:
./easyrsa gen-req client1 ./easyrsa sign-req client client1 |
Congratulations, all certificates have been generated. You will need the following four files in order to configure the client side of the VPN:
/etc/openvpn/easy-rsa/pki/ca.crt /etc/openvpn/easy-rsa/pki/issued/client1.crt /etc/openvpn/easy-rsa/pki/private/client1.key /etc/openvpn/mykey.tls |
SYSTEM CONFIGURATION
In order to enable routing, some firewall rules have to be defined. We will use firewalld in this example but other firewalls such as CSF or the basic iptables work as well.
Add the openvpn service to the list of trusted zones and check if it was included correctly:
firewall-cmd --zone=trusted --add-service openvpn firewall-cmd --zone=trusted --add-service openvpn --permanent firewall-cmd --list-services --zone=trusted |
Configure a masquerade both on your current instance and permanently:
firewall-cmd --add-masquerade firewall-cmd --permanent --add-masquerade |
Create a variable, then use it to add a permanent routing rule on your main network interface:
VAR=$(ip route get 8.8.8.8 | awk 'NR==1 {print $(NF-2)}') firewall-cmd --permanent --direct --passthrough ipv4 -t nat -A POSTROUTING -s 10.8.0.0/24 -o $VAR -j MASQUERADE |
The final step is to reload firewalld in order to implement all these changes:
1 | firewall-cmd –reload |
In CentOS, packet forwarding is disabled by default but you can easily enable it by editing the file /etc/sysctl.conf and adding the line:
1 | net.ipv4.ip_forward=1 |
Execute the following commands to restart the network with the new rules:
sysctl –p systemctl restart network |
START THE SERVICE
Everything is now configured, it is time to start the service and enable it, so it loads automatically every time the system reboots:
systemctl start openvpn@server.service systemctl enable openvpn@server.service |
Check if everything is in order, the command output should be active (running):
1 | systemctl status openvpn@server.service |
CONFIGURE A WINDOWS CLIENT
Assuming your local desktop/laptop runs Window, you will want to set up a client to connect to your VPN server.
Download and execute the installer from OpenVPN’s website, the application must be run with administrator rights.
The default configuration folder is /Program Files/OpenVPN/config, copy the four files (ca.crt, client1.crt, client1.key and mykey.tls) there.
Create a new file named client.ovpn in the same folder, with the following content (replace IP with the actual IP address of your OpenVPN server):
client tls-client remote <IP> 443 proto tcp resolv-retry infinite route-delay 2 pull dev tun nobind ca ca.crt cert client1.crt key client1.key tls-crypt mykey.tls remote-cert-eku "TLS Web Client Authentication" topology subnet pull user nobody group nobody |
After stating the application, the OpenVPN GUI icon is located in the system tray. Right click on it and click Connect to start using the service.
CONNECT FROM OTHER OPERATING SYSTEMS
If you own a Mac, there are several VPN clients available, we recommend a free software called Tunnelblick. Install it from the App Store, then copy the same four files from your server and create a client.ovpn identical to the Windows one.
Make sure that all these files are in the same folder, then open the application, navigate to the folder and click on the client.ovpn file. The VPN is now installed and you only have to click on Connect in order to use it.
If Linux is your OS of choice, install the openvpn client using your distribution’s native package manager. The package is not available in the default repositories of some distributions, so you might have to enable additional ones (for example EPEL in the RedHat OS family).
Just like in Windows and Mac, you need the four files from the server, as well as a client.ovpn file with the same content.
Run the application from the command line with the root user or sudo privileges, make sure that you include the full path to the .ovpn file:
1 | openvpn --config client.ovpn |
After you connect, use a website that displays your public IP (Google “What is my IP” for a few options) in order to check that Internet traffic is now properly routed through the VPN.
FINAL CONSIDERATIONS
We have only described the basic server setup in this article, but OpenVPN is a very powerful application that can be customized further. Read the official documentation for various tutorials and use case scenarios.
You now have a fully functional virtual private network server that allows you to browse the Internet anonymously and prevents all types of tracking.
By running a VPN server on your own VPS, you can configure the service based on your specific needs and allow connections from multiple clients, for a price that is cheaper than a single commercial VPN subscription.
Categories
- cPanel Question 47
- cPanel Software Management 29
- cPanel Tutorials 13
- Development 29
- Domain 13
- General 19
- Linux Helpline (Easy Guide) 156
- Marketing 47
- MySQL Question 13
- News 2
- PHP Configuration 14
- SEO 4
- SEO 42
- Server Administration 84
- SSL Installation 54
- Tips and Tricks 24
- VPS 3
- Web Hosting 44
- Website Security 22
- WHM questions 13
- WordPress 148
Subscribe Now
10,000 successful online businessmen like to have our content directly delivered to their inbox. Subscribe to our newsletter!Archive Calendar
| Sat | Sun | Mon | Tue | Wed | Thu | Fri |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | 31 | |||
Recent Articles
-

Posted on : Sep 17
-

Posted on : Sep 10
-

Posted on : Aug 04
-

Posted on : Apr 01
Tags
- ts
- myisam
- vpn
- sql
- process
- kill
- tweak
- server load
- attack
- ddos mitigation
- Knowledge
- layer 7
- ddos
- webmail
- DMARC
- Development
- nginx
- seo vpn
- Hosting Security
- wireguard
- innodb
- exim
- smtp relay
- smtp
- VPS Hosting
- cpulimit
- Plesk
- Comparison
- cpu
- encryption
- WHM
- xampp
- sysstat
- optimize
- cheap vpn
- php-fpm
- mariadb
- apache
- Small Business
- Error
- Networking
- VPS
- SSD Hosting
- Link Building
- centos
- DNS
- optimization
- ubuntu