What is an SSL certificate and what is it used for?
- Category : SSL Installation
- Posted on : May 17, 2021
- Views : 1,720
- By : HostSEO

1. Introduction
SSL certificates are used to create an encrypted channel between the client and the server. Transmission of such data as credit card details, account login information, any other sensitive information has to be encrypted to prevent eavesdropping.
With an SSL certificate, data is encrypted prior to being transmitted via Internet. Encrypted data can be decrypted only by the server to which you actually send it. This ensures that the information you submit to websites will not be stolen.
Starting from 06/08/2014, Google announced that having an SSL certificate installed on your website will increase your ranking position, which is another great reason to use an SSL.
The certificate itself represents base64 encoded data that contains information about the entity the certificate was issued for, public key required for encryption and digital signature verification, and digital signature created with the private key of the certificate issuer.

An SSL certificate has to be installed on the server side. When you access a website secured by an SSL certificate issued by a trusted Certification Authority, you will see https:// at the beginning of its URL. A browser will also show the connection as secure by displaying a â$œlockâ$ icon in the address bar:
![]()
2. Types of SSL certificates
SSL certificates can be divided into 3 validation groups:
Domain Validation Certificates
Requires a certificate applicant to prove his/her control over the domain name only. The issued certificate contains a domain name that was supplied to the Certification Authority within the certificate request.
Organization Validation Certificates
Requires a certificate applicant to prove that his/her company is a registered and legally accountable business, and to pass domain validation. The issued certificate contains a domain and company name of the certificate applicant.
Extended Validation Certificates
Includes validation requirements of two validation types mentioned above and additional requirements. The issued certificate contains a domain and company name of the certificate applicant.
Technical Overview
Glossary
- Asymmetric cryptography - ciphers that imply different keys for encryption and decryption processes
- Cipher suite - set of key exchange, authentication, encryption and message authentication code (MAC) algorithms used within SSL/TLS protocols
- Handshake - protocol use within SSL/TLS for the purpose of security parameters negotiation
- Key exchange - in the context of SSL/TLS, the way client and server securely establish a pre-master secret for a session
- Master secret - key material used for generation of encryption keys, MAC secrets and initialization vectors (IVs)
- Message Authentication Code (MAC) - one-way hash function computed over a message and a secret
- Pre-master secret - key material used for the master secret derivation
- Symmetric cryptography - ciphers that imply the same key both for encryption and decryption processes
4. Symmetric & Asymmetric cryptography
Two types of cryptography are being used by SSL/TLS protocols: symmetric and asymmetric.
Symmetric cryptography (also called â$œbulk encryptionâ$) implies the same key for encryption as well as for decryption. In SSL/TLS symmetric ciphers are generally used for application data encipherment.
Examples of symmetric ciphers: AES, RC4, DES
Asymmetric cryptography (also called â$œpublic key cryptographyâ$) implies different keys for encryption and decryption.
Public key contained in a CSR and subsequently in an SSL certificate is used for encryption and signature verification. A private key which is typically kept on the server may be used, depending on the cipher suite negotiated during the handshake, either for decryption of a pre-master secret required for computation of a master secret, or for signing parameters required to compute a master secret.
In plain words, in the context of SSL/TLS protocols, asymmetric encryption serves the purpose of secure symmetric encryption key computation for both sides (client/server).
Example of asymmetric cryptosystems: RSA, DHE, ECDHE
5. Cipher Suite
Cipher suite is a set of key exchange, authentication, encryption and message authentication code (MAC) algorithms used within SSL/TLS protocols.
Examples:
Cipher suite TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 implies
- DHE for key exchange
- RSA for authentication
- AEC_256_GCM for bulk encryption
- SHA384 is a hash function used for MAC computations
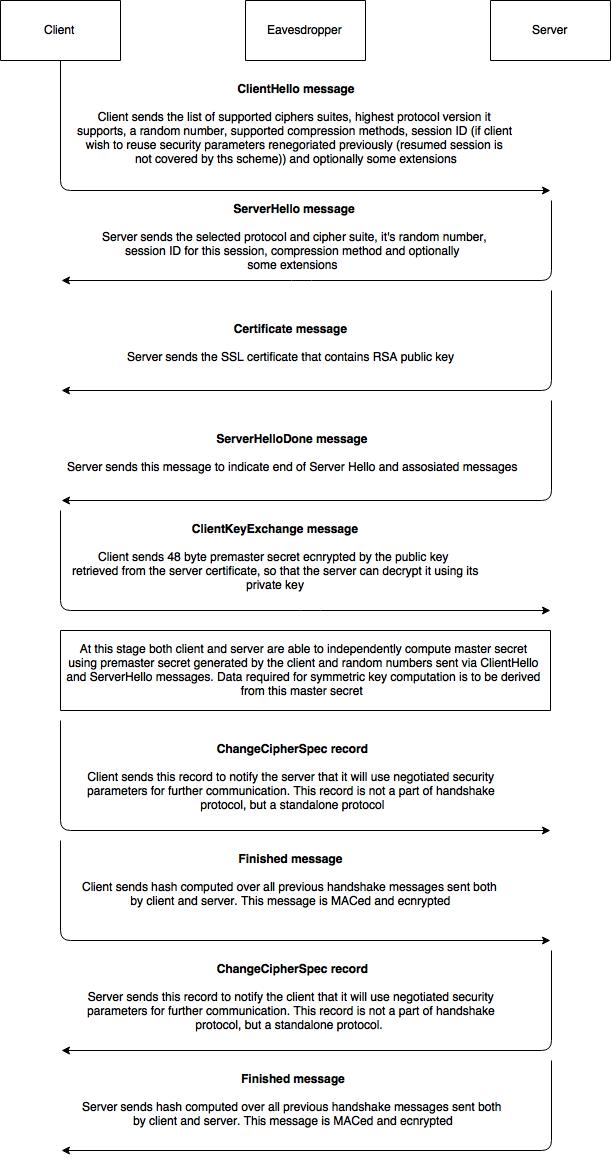
6. Handshake
Handshake is a protocol used within SSL/TLS for the purpose of security parameters negotiation. Depending on the cipher suite, a handshake can consist of different messages that parties send to each other.
The diagram below describes one of the most common handshake message flows that imply premaster key encipherment with an RSA public key. Such a handshake message flow is applicable for cipher suites as follows (examples):
TLS_RSA_WITH_RC4_128_MD5
TLS_RSA_WITH_RC4_128_SHA
TLS_RSA_WITH_3DES_EDE_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_256_GCM_SHA384
Categories
- cPanel Question 47
- cPanel Software Management 29
- cPanel Tutorials 13
- Development 29
- Domain 13
- General 19
- Linux Helpline (Easy Guide) 156
- Marketing 47
- MySQL Question 13
- News 2
- PHP Configuration 14
- SEO 4
- SEO 42
- Server Administration 84
- SSL Installation 54
- Tips and Tricks 24
- VPS 3
- Web Hosting 44
- Website Security 22
- WHM questions 13
- WordPress 148
Subscribe Now
10,000 successful online businessmen like to have our content directly delivered to their inbox. Subscribe to our newsletter!Archive Calendar
| Sat | Sun | Mon | Tue | Wed | Thu | Fri |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | ||||||
Recent Articles
-

Posted on : Sep 17
-

Posted on : Sep 10
-

Posted on : Aug 04
-

Posted on : Apr 01
Tags
- ts
- myisam
- vpn
- sql
- process
- kill
- tweak
- server load
- attack
- ddos mitigation
- Knowledge
- layer 7
- ddos
- webmail
- DMARC
- Development
- nginx
- seo vpn
- Hosting Security
- wireguard
- innodb
- exim
- smtp relay
- smtp
- VPS Hosting
- cpulimit
- Plesk
- Comparison
- cpu
- encryption
- WHM
- xampp
- sysstat
- optimize
- cheap vpn
- php-fpm
- mariadb
- apache
- Small Business
- Error
- Networking
- VPS
- SSD Hosting
- Link Building
- centos
- DNS
- optimization
- ubuntu