HOW TO SET UP TLS ON CPANEL SERVERS
- Category : Server Administration
- Posted on : Oct 14, 2017
- Views : 2,834
- By : Edgardo D.

Transport Layer Security (TLS), and it’s older brother Secure Socket Layer (SSL) are cryptographic protocols that clients and servers use for secure communication over the Internet. Today’s industry standards, and really just common sense, strongly encourage the use of cryptography. This is especially important if you’re running a webshop or any kind of site that accepts credit card payments, as your site and server will have to be PCI compliant. In this article, we’ll see how to set up TLS protocols and ciphers for various services.
A FOREWORD
Luckily, cPanel is keeping up with industry standards. In version 72, they removed support for SSLv2, SSLv3 and TLSv1.0, with only TLSv1.2 being enabled by default. If you keep you system up to date, chances are high you won’t need to manually configure anything, except in the case you need backwards compatibility for older versions of web browsers and mail clients.
The services we’ll set up here use OpenSSL to provide both the protocols and ciphers that will be in use. Hence, if you’re configuring TLS manually, you’ll probably have to configure both.
APACHE (HTTPD SERVICE)
To configure TLS for Apache, i.e. your web server, go to WHM > Home > Service Configuration > Apache Configuration > Global Configuration. The protocol and cipher settings will be the first two in that interface:
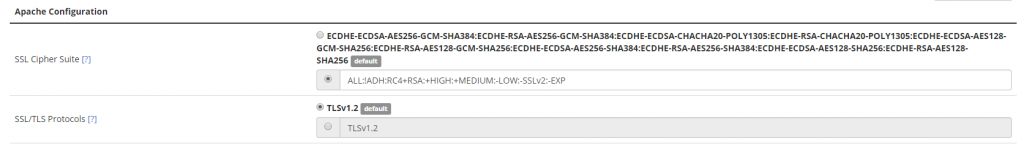
This interface accepts a protocol string such as All -SSLv2 -SSLv3 . If you need to enable TLSv1.1, add either:
1 | All -SSLv2 -SSLv3 -TLSv1 |
or
1 | TLSv1.2 TLSv1.1 |
Setting up the cipher suite is where it gets tricky. On versions 68 and above, cPanel uses the following cipher suite for it’s default:
1 | ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256 |
This should work fine for TLS 1.1 and 1.2, and is designed for more compatibility than security, but if you need to edit this, here are some general rules:
Usually, the client’s preference will be used when choosing the protocol and cipher that will be used when establishing a secure connection. If you want to use the server’s preference, add the following lines in /usr/local/apache/conf/includes/pre_virtualhost_global.conf via CLI, or in Home > Service Configuration > Apache Configuration > Include Editor > Pre VirtualHost Include:
<IfModule ssl_module> SSLHonorCipherOrder On </IfModule> |
If you edited this file via CLI, you’ll have to rebuild httpd.conf with /scripts/rebuildhttpdconf and restart Apache with service httpd restart for these changes to take effect.
Each cipher can have one of the following prefixes:
- none: add cipher to list
- +: move matching ciphers to the current location in list
- -: remove cipher from list (can be added later again)
- !: kill cipher from list completely (can not be added later again)
Be wary of using the ! Prefix, as you won’t be able to add that cipher at a later time. By using these prefixes you can get really granular in setting up the cipher suite, and combined with the SSLHonorCipherOrder you can ensure the server will always use the strongest available cipher.
The following ciphjer suite list might be more secure than the default one:
1 | ALL:!ADH:RC4+RSA:+HIGH:+MEDIUM:-LOW:-SSLv2:-SSLv3:-TLSv1:-EXP:!kEDH:!aNULL |
but it’s possible you’ll have to play around with this to get the optimal amount of security vs backwards compatibility, that A score on Qualys, or to pass your PCI compliance scans.
EXIM (THE MAIL TRANSFER AGENT)
If you’re running a mail server, you’ll probably want all the mail clients to connect to it securely. The first thing you need to do is go to Home > Service Configuration > Exim Configuration Manager > Security tab, and turn on the option called Require clients to connect with SSL or issue the STARTTLS command before they are allowed to authenticate with the server . This option will prevent non-secure connections.
As for the protocol setup, on versions 68 and above, the default setting is +no_sslv2 +no_sslv3 +no_tlsv1 +no_tlsv1_1 so feel free to leave it at that. If you do need TLS 1.1 enabled, change the setting to
1 | +no_sslv2 +no_sslv3 +no_tlsv1 |
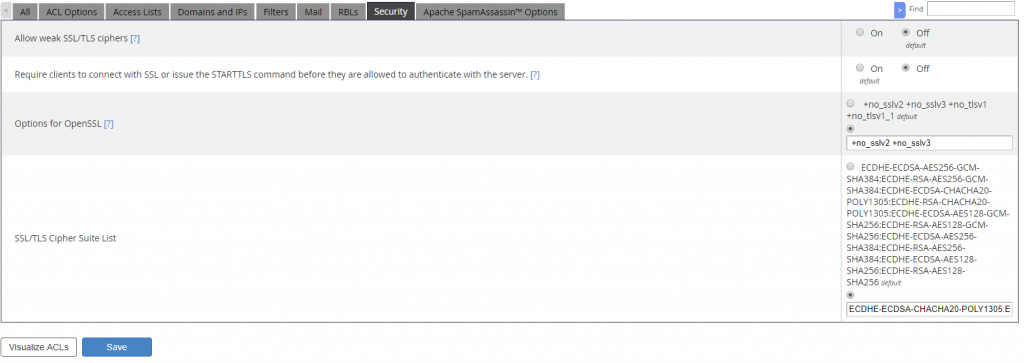
Once again, the default ciphers are okay to use, but if you need backwards compatibility for older mail client and operating systems such as Windows XP, replace it with this cipher suite:
ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS |
DOVECOT (THE MAIL SERVER)
To change the protocols and cipher suites for your mail server, navigate to WHM > Home > Service Configuration > Mailserver Configuration:
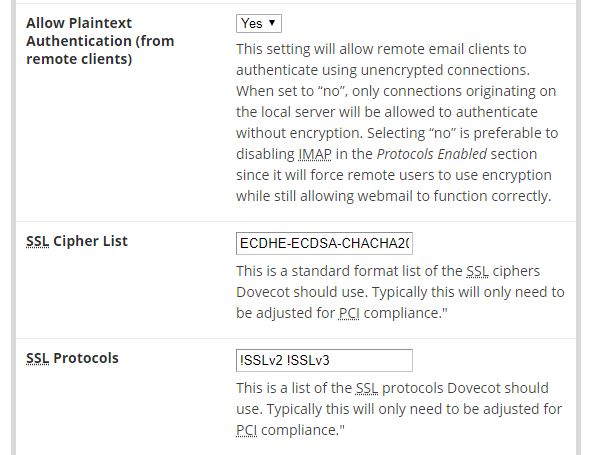
The SSL protocol field accepts a string that implies ALL by default, such as !SSLv2 !SSLv3, similar to Apache. To disable TLS 1.0, replace the protocols with this:
1 | !SSLv2 !SSLv3 !TLSv1 |
Feel free to leave the ciphers at their defaults, or replace them with ones from the Exim section for backwards compatibility.
Also, turn off the Allow Plaintext Authentication (from remote clients) option to make sure all mail clients are connecting securely to your mail server.
CPANEL & WHM (CPSRVD)
To set this up, navigate to WHM > Home > Service Configuration > cPanel Web Services Configuration:
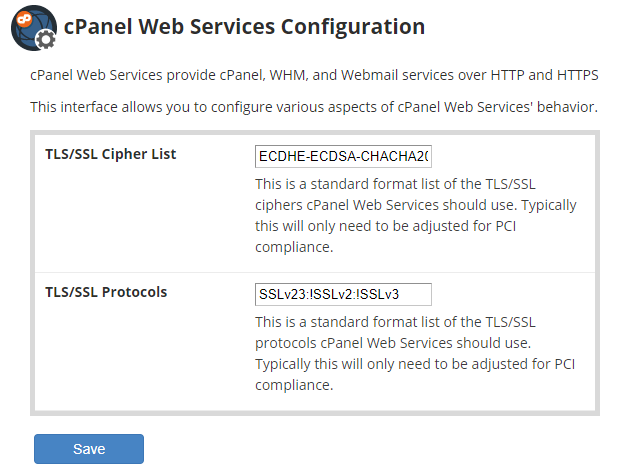
These settings will affect all cPanel and WHM logins. As many server compromises happen because of compromised passwords, you’ll want to have this as secure as possible. In order to do that, replace the default protocols with the following line:
1 | SSLv23:!SSLv2:!SSLv3:!TLSv1:!TLSv1_1 |
to enable TLS 1.2 only, or
1 | SSLv23:!SSLv2:!SSLv3:!TLSv1 |
if you need TLS 1.1 enabled.
The cipher suite is PCI compliant so there should be no need to change it.
CONCLUSION
Luckily, setting up TLS on a cPanel isn’t all that difficult, thanks to their graphical interface. If you have no specific requirements of your server, or if you’re not hosting any webshops or similar sites, there should be no need for you to edit these settings. If you need to edit them, however, it is our hope this post helped you out in making your server as secure as possible!
Categories
- cPanel Question 47
- cPanel Software Management 29
- cPanel Tutorials 13
- Development 29
- Domain 13
- General 19
- Linux Helpline (Easy Guide) 156
- Marketing 47
- MySQL Question 13
- News 2
- PHP Configuration 14
- SEO 4
- SEO 42
- Server Administration 84
- SSL Installation 54
- Tips and Tricks 24
- VPS 3
- Web Hosting 44
- Website Security 22
- WHM questions 13
- WordPress 148
Subscribe Now
10,000 successful online businessmen like to have our content directly delivered to their inbox. Subscribe to our newsletter!Archive Calendar
| Sat | Sun | Mon | Tue | Wed | Thu | Fri |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | 31 | |||
Recent Articles
-

Posted on : Sep 17
-

Posted on : Sep 10
-

Posted on : Aug 04
-

Posted on : Apr 01
Tags
- ts
- myisam
- vpn
- sql
- process
- kill
- tweak
- server load
- attack
- ddos mitigation
- Knowledge
- layer 7
- ddos
- webmail
- DMARC
- Development
- nginx
- seo vpn
- Hosting Security
- wireguard
- innodb
- exim
- smtp relay
- smtp
- VPS Hosting
- cpulimit
- Plesk
- Comparison
- cpu
- encryption
- WHM
- xampp
- sysstat
- optimize
- cheap vpn
- php-fpm
- mariadb
- apache
- Small Business
- Error
- Networking
- VPS
- SSD Hosting
- Link Building
- centos
- DNS
- optimization
- ubuntu