Installing an SSL certificate on Nginx
- Category : SSL Installation
- Posted on : Sep 07, 2020
- Views : 1,514
- By : HostSEO

Upload the certificates on the server where your website is hosted
Having completed the CSR code generation and SSL activation steps, you will receive a zip file with the Sectigo (previously known as Comodo) Certificates via email. Alternatively, you can download them from your Namecheap Account panel.
Note: If you choose NGINX server when activating the certificate, you'll receive a zip file containing a Certificate file, with the '.crt' extension, and a Certificate Authority (CA) bundle file, with the '.ca-bundle' extension.
Upload both files to your server whatever way you prefer. By using an FTP client, for example.
You can also download the Bundle file for each Certificate by following the instructions here.
Combine all the certificates into a single file
You need to have all the Certificates (your_domain.crt and your_domain.ca-bundle) combined in a single '.crt' file.
The Certificate for your domain should come first in the file, followed by the chain of Certificates (CA Bundle).
Enter the directory where you uploaded the certificate files. Run the following command to combine the files:
$ cat your_domain.crt your_domain.ca-bundle >> your_domain_chain.crtPlease note that if the certificate files were downloaded from your Namecheap account, the best command to use will be:
$ cat your_domain.crt > your_domain_chain.crt ; echo >> your_domain_chain.crt ; cat your_domain.ca-bundle >> your_domain_chain.crt
Alternatively, you can combine the files using this online tool and following the steps below:- Open your_domain.crt file in a text editor and copy the certificate code, including the '-----BEGIN CERTIFICATE-----' and '-----END CERTIFICATE-----' tags.
- Go to decoder.link and open the SSL&CSR Decoder tab.
- Paste your_domain.crt text code to the required field and hit Decode.
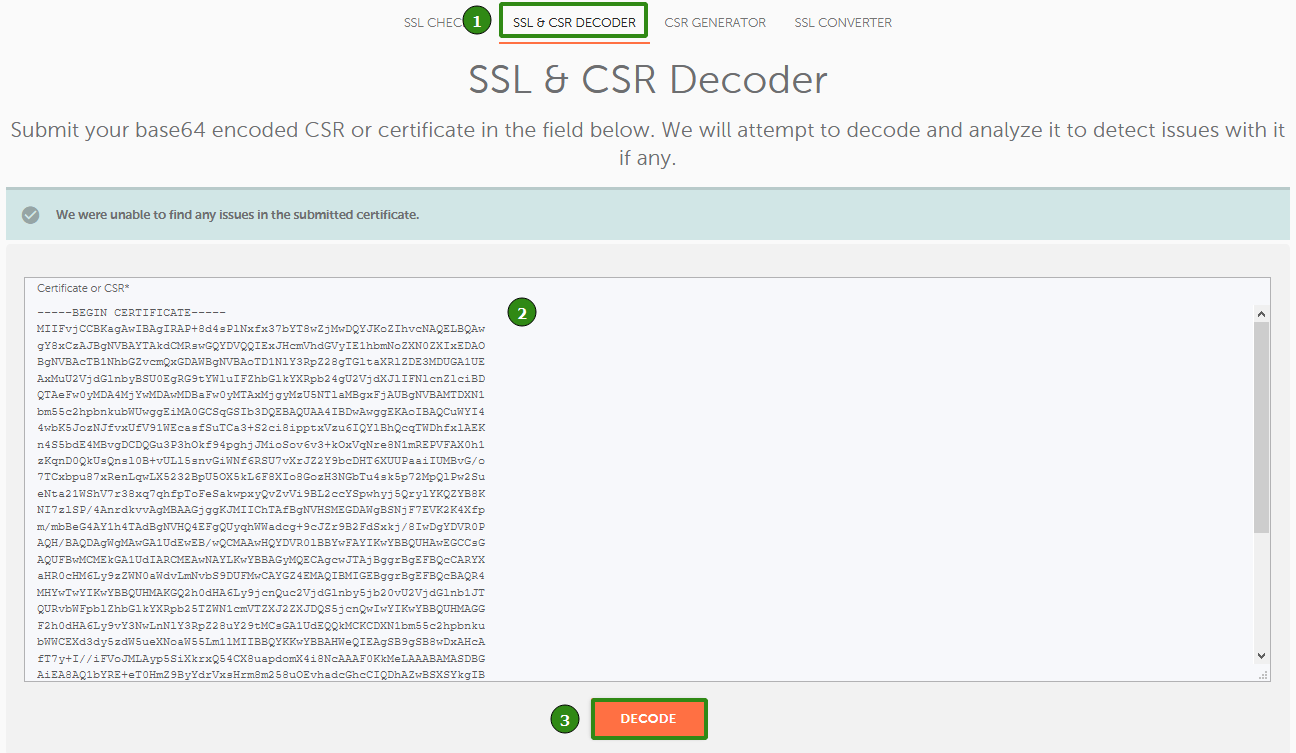
- Next, scroll down the results and find Bundle (Nginx) section within the General Information part.
- Click on the floppy disk icon over on the right to download the generated file.
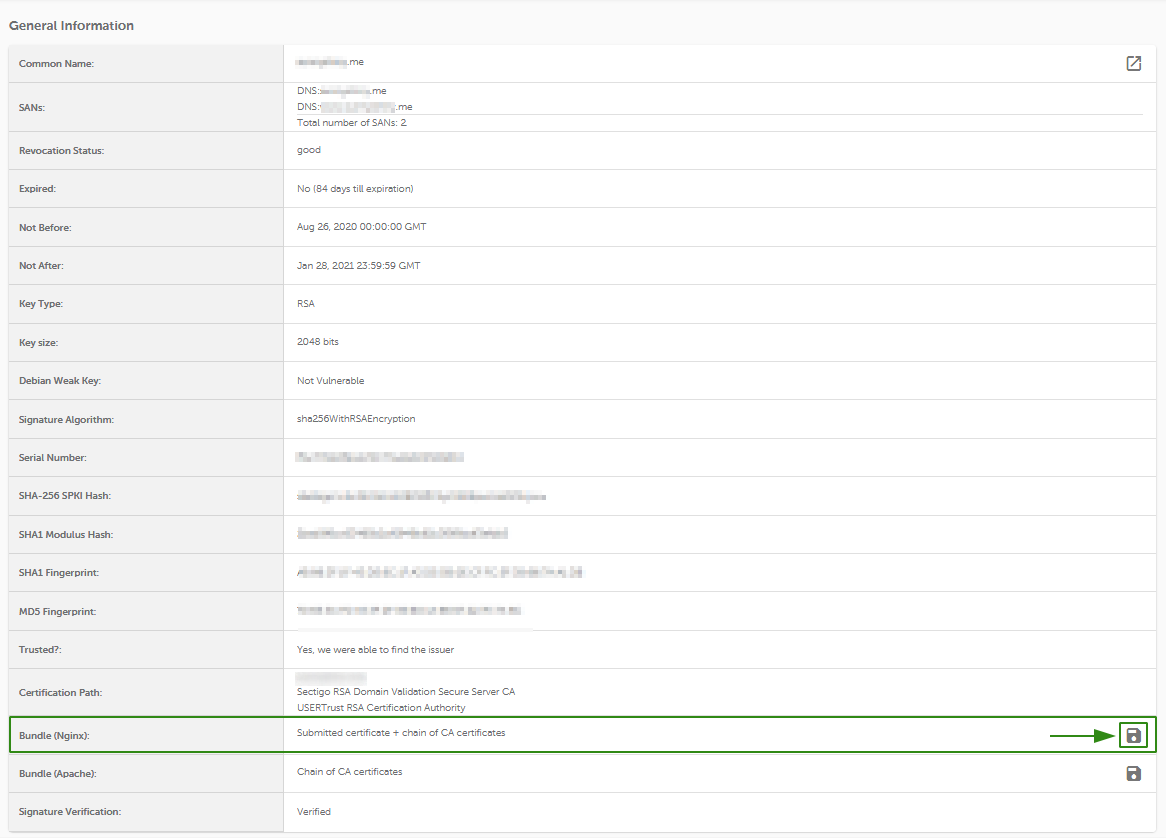
- The 'nginx_bundle.zip' file will be downloaded to your PC. Unzip it and use the nginx_bundle_l3s4k9n1l0s3.crt file (the 'l3s4k9n1l0s3' part of the name is a random alphanumeric string) for installation.
That's it!
Creating a separate Nginx server block or Modifying the existing configuration file
To install the SSL certificate on Nginx, you need to show the server which files to use, either by a) creating a new configuration file, or b) editing the existing one.
   a) By adding a new configuration file for the website you can make sure that there are no issues with the separate configuration file. Furthermore, it will be quite easier to troubleshoot the installation in case of any issues with the new configuration.
We suggest creating a new configuration file in this folder:
/etc/nginx/conf.dThat can be done via this command:
sudo nano /etc/nginx/conf.d/Your_domain*-ssl.confWhere
Next, copy and paste one of the below server blocks for the 443 port and edit the directories. Ensure the server name and path to webroot match in both the server block for port 80 and the one for port 443. If you have any other important values that need to be saved, move them to the newly created server block too.Your_domain*-ssl.confis the name of the newly created file.   b) Edit the default configuration file of the web-server, which is named
nginx.conf. It should be in one of these folders:/usr/local/nginx/conf/etc/nginx/usr/local/etc/nginxYou can also use this command to find it:
sudo find / -type f -iname "nginx.conf"Once you find it, open the file with:
sudo nano nginx.confThen copy and paste one of the server blocks for the 443 port given below and edit the directories according to your server block for the 80 port (with matching server name, path to webroot, and any important values you need). Alternatively you can copy the server block for 80 port, then paste it below, update the port and add the necessary SSL-related directives.
Choose the server block:
Below you can find a server block for your Nginx version.
Note: To check your Nginx version, run this command:
sudo nginx -v
Note: Replace the file names values, like
your_domain_chain.crt, in the server block with your details, and modify the routes to them using/path/to/.- Server block for Nginx version 1.14 and below:
server {listen 443;ssl on;ssl_certificate /path/to/certificate/your_domain_chain.crt;ssl_certificate_key /path/to/your_private.key;root /path/to/webroot;server_name your_domain.com;}
Note: You can specify multiple hostnames in such configuration, if needed, e.g.:
server {listen 443;ssl on;ssl_certificate /path/to/certificate/your_domain_chain.crt;ssl_certificate_key /path/to/your_private.key;root /path/to/webroot;server_name your_domain.com www.your_domain.com;}
- Server block for Nginx version 1.15 and above:
server {listen 443 ssl;ssl_certificate /path/to/certificate/your_domain_chain.crt;ssl_certificate_key /path/to/your_private.key;root /path/to/webroot;server_name your_domain.com;}
ssl_certificateshould be pointed to the file with combined certificates youâ$™ve created earlier.ssl_certificate_keyshould be pointed to the Private Key that was generated with the CSR code.
Here are a few tips on how to find the Private key on Nginx.
Important: For either a Multi-Domain or a Wildcard Certificate, youâ$™ll need to have a separate server block added for each of the domain/subdomain included in the Certificate. Ensure you specify the domain/subdomain in question along with the paths to the same Certificate files in the server block, as described above.Once the corresponding server block is added to the file, ensure you save the edits. Then, you can double-check the changes made with the following steps.
Run this command to verify that the configuration file syntax is ok:
sudo nginx -t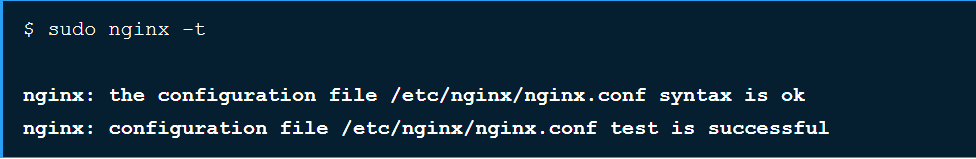
If you receive errors, double check that you followed the guide properly. Feel free to contact our Support Team if you have any questions.
Here's the tip: to find the error logs for troubleshooting, just run:sudo nginx -T | grep 'error_log'In case none of the files mentioned exist, files are commented out or if no error log files are specified, default system log should be checked:
tail /var/log/nginx/error.log -n 20If the server displays the test successfully, restart Nginx with this command to apply the changes:
sudo nginx -s reloadNow your SSL Certificate is installed. You can check the installation here.
Important notes:
Sometimes, after installing SSL file that was combined using a command line, you may receive 'Nginx/Apache error: 0906D066:PEM routines:PEM_read_bio:bad end line' error message, in this case, the workaround can be found in the reference guide.
Another common issue on this stage is the 'Nginx SSL: error:0B080074:x509 certificate routines: X509_check_private_key:key values mismatch' error message, you can find more details on it and the possible ways out in this article.
Configure HTTPS redirect
We suggest that you install the redirect from HTTP to HTTPS. That way, your website visitors will only be able to access the secure version of your site.
To do this, youâ$™ll need to add one line to the configuration file with the server block for port 80.
Tips:
- You can use one of the following commands to look up the configuration files which are enabled now:
sudo nginx -T | grep -iw "configuration file"sudo nginx -T | grep -iw "include"- The default paths to the conf file are:
on RHEL-based Linux OS:
/etc/nginx/conf.d/default.confon Debian-based Linux OS:
/etc/nginx/sites-enabled/default- You can open the files to check which one contains the needed server block. For this, run:
sudo nano name_of_the_fileOnce you find the file that contains the server block for port 80 (the default HTTP port), add in the following line:
return 301 https://$server_name$request_uri;Note: The above redirect rule should be entered as the last line in the server block.returnis the main directive to use.301is permanent redirect (302 is the temporary one).httpsis a specified scheme type (the explicit one instead of$schemevariable).$server_namevariable will use the domain specified in the server_name directive.$request_urivariable is used to match the paths to the requested pages/parts of the website (everything after the domain name).
Here are examples of server blocks with the HTTPS redirect:
Permanent redirect to HTTPS
server {listen 80;server_name your_domain.com www.your_domain.com;return 301 https://$server_name$request_uri;}Permanent redirect to HTTPS non-www
server {listen 80;server_name your_domain.com www.your_domain.com;return 301 https://your_domain.com$request_uri;}Permanent redirect to HTTPS www
server {listen 80;server_name your_domain.com www.your_domain.com;return 301 https://www.your_domain.com$request_uri;}Temporary redirect to HTTPS non-www
server {listen 80;server_name your_domain.com www.your_domain.com;return 302 https://your_domain.com$request_uri;}You can find more details about redirect options on Nginx here.
- You can use one of the following commands to look up the configuration files which are enabled now:
Categories
- cPanel Question 47
- cPanel Software Management 29
- cPanel Tutorials 13
- Development 29
- Domain 13
- General 19
- Linux Helpline (Easy Guide) 156
- Marketing 47
- MySQL Question 13
- News 2
- PHP Configuration 14
- SEO 4
- SEO 42
- Server Administration 84
- SSL Installation 54
- Tips and Tricks 24
- VPS 3
- Web Hosting 44
- Website Security 22
- WHM questions 13
- WordPress 148
Subscribe Now
10,000 successful online businessmen like to have our content directly delivered to their inbox. Subscribe to our newsletter!Archive Calendar
| Sat | Sun | Mon | Tue | Wed | Thu | Fri |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | 31 | |||
Recent Articles
-

Posted on : Sep 17
-

Posted on : Sep 10
-

Posted on : Aug 04
-

Posted on : Apr 01
Tags
- ts
- myisam
- vpn
- sql
- process
- kill
- tweak
- server load
- attack
- ddos mitigation
- Knowledge
- layer 7
- ddos
- webmail
- DMARC
- Development
- nginx
- seo vpn
- Hosting Security
- wireguard
- innodb
- exim
- smtp relay
- smtp
- VPS Hosting
- cpulimit
- Plesk
- Comparison
- cpu
- encryption
- WHM
- xampp
- sysstat
- optimize
- cheap vpn
- php-fpm
- mariadb
- apache
- Small Business
- Error
- Networking
- VPS
- SSD Hosting
- Link Building
- centos
- DNS
- optimization
- ubuntu