Installing an SSL certificate on Amazon Web Services (AWS)
- Category : SSL Installation
- Posted on : Feb 01, 2021
- Views : 1,072
- By : HostSEO

Amazon Web Services provides hosting instances that can be used to host both common servers and applications, as well as some specific additional services. Because of this, there are multiple options for installing an SSL certificate on AWS.
- Some prerequisite information
- Elastic Compute Cloud (EC2)
- Elastic Load Balancer (ELB)
- AWS API Gateway
- Amazon CloudFront
Some prerequisite information
For SSL installation you generally need three components: a certificate, an intermediate certificate chain (CA-bundle) and a Private key.
- SSL Certificates are sent as a PEM-formatted file with a .crt extension. If the extensions are not shown in your system by default for all files, an SSL will have "Security certificate" in the file description. The same file can be also downloaded this way.
Inside the file there is a code like this:

- An Intermediate certificate chain (CA-bundle) is also sent in a PEM-format file, but this file has a .ca-bundle extension. Inside the file, there are normally one or two codes similar to the certificate. The CA-bundle, as with the certificate, is usually in the SSL archive you receive after SSL activation. It can also be downloaded here.
- A Private key is generated along with the certificate signing request (CSR) used to activate your SSL. If you generated the CSR on your server, the key is saved in the same place. It has .key extension.
It contains a code like this:

Elastic Compute Cloud (EC2)
sudo yum install -y mod24_ssl
Elastic Load Balancer (ELB)
- The first option is pretty simple. During the Load balancer creation you can import the new certificate in the second step of the setup:
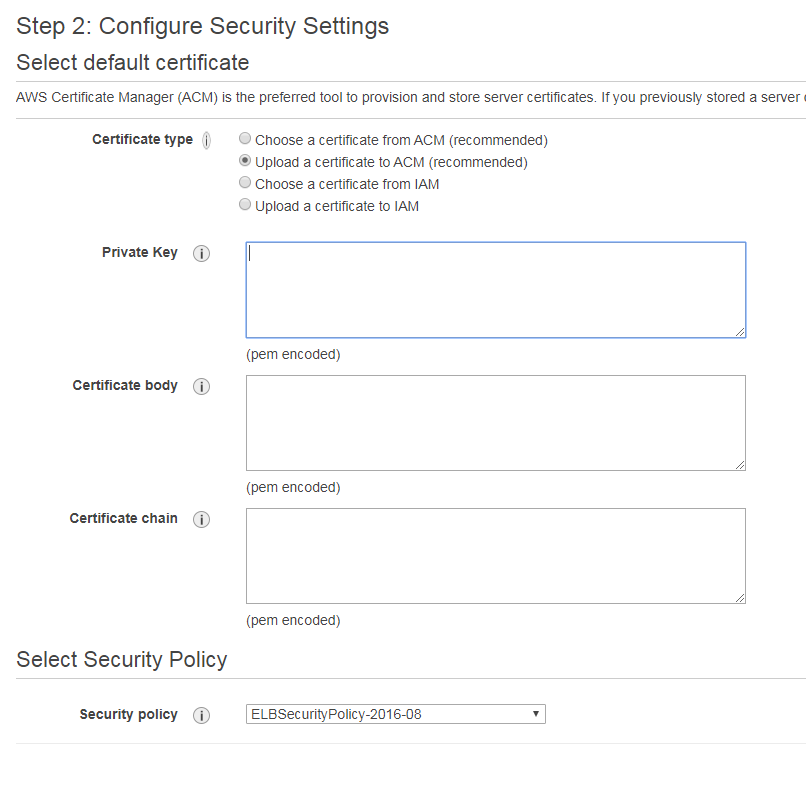
Simply choose to upload the certificate to ACM (this option sets a default SSL for all unassigned cases) or IAM (this one allows you to add multiple SSLs) and paste all 3 SSL components as codes:
- The Certificate in the "Certificate body" form;
- CA-bundle in the "Certificate chain" form;
- And the Private key in the "Private key" form.
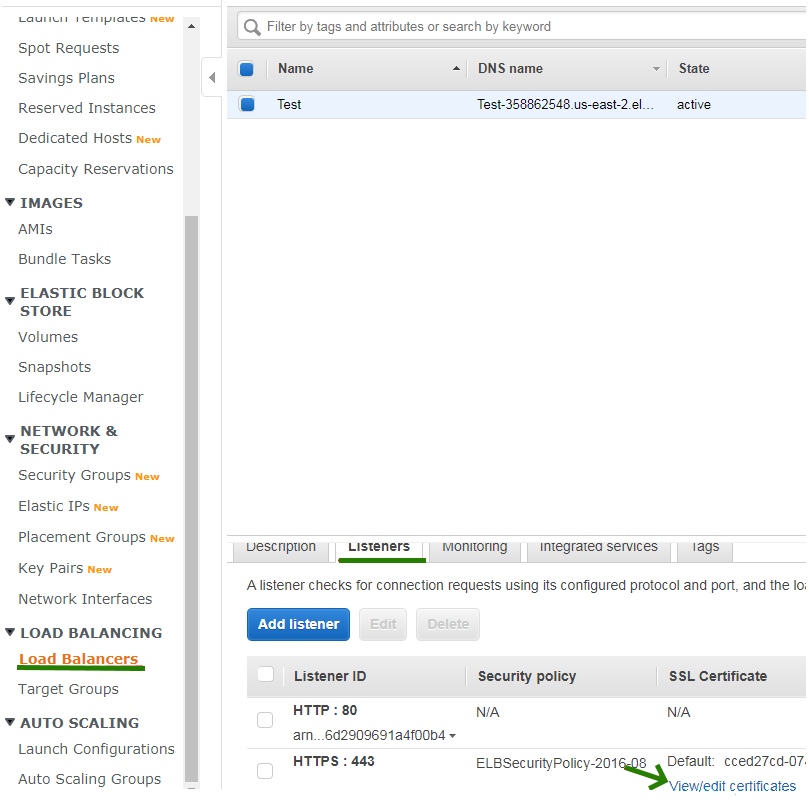
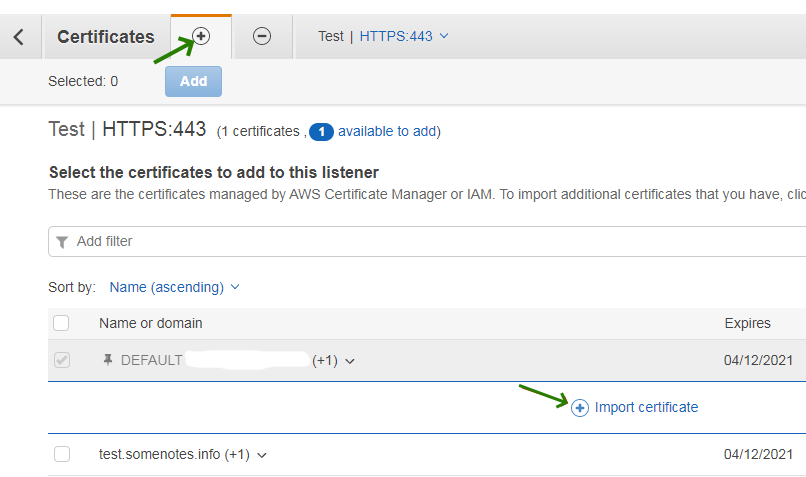
- For the second option, upload the certificate, Private key and CA Bundle to your server and open the command line. All three files can be installed using a single command:
certificate-body and private-key parameters), file:// should be included as a part of the file name.- Certificates should be in X.509 PEM format.
- The current date should be between the certificate’s issuance and expiration date.
- The certificate and Private key files should contain only a single item, meaning one certificate file and one corresponding key.
- The Private key should match the certificate.
- The Private key should be in PEM format, just like the certificate is. The correct format of the text within the key file should begin with -----BEGIN RSA PRIVATE KEY----- and ends with -----END RSA PRIVATE KEY-----.
- The Private key should not be encrypted with a password.
arn:aws:iam::Your_AWS_Account_ID:server-certificate/Your_Certificate_Object_Name Certificate_Object_GUID<
- If you need to update the certificate for a HTTPS load balancer, you will need to use the ARN of the certificate. The following command is used in such a case to set the certificate for the load balancer:
my-loadbalancer is the name of your load balancer.AWS API Gateway
- Log in to the AWS Certificate Manager console.
- Choose the Import a certificate option.
- A similar form for the SSL upload will open.
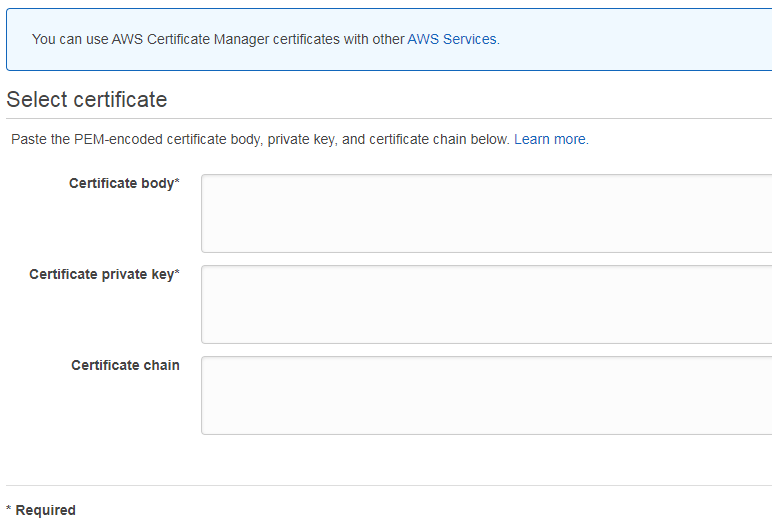
- Paste the certificate file code as the "Certificate body", CA-bundle code as the "Certificate chain" and Private key code as the "Certificate private key" and click Next.
- Save the changes by selecting the Review and import option.
- Choose the Custom domain names option from the API Gateway menu.
- Choose your custom domain name.
- Click Edit.
- Choose the correct SSL from the drop-down list and save the changes.
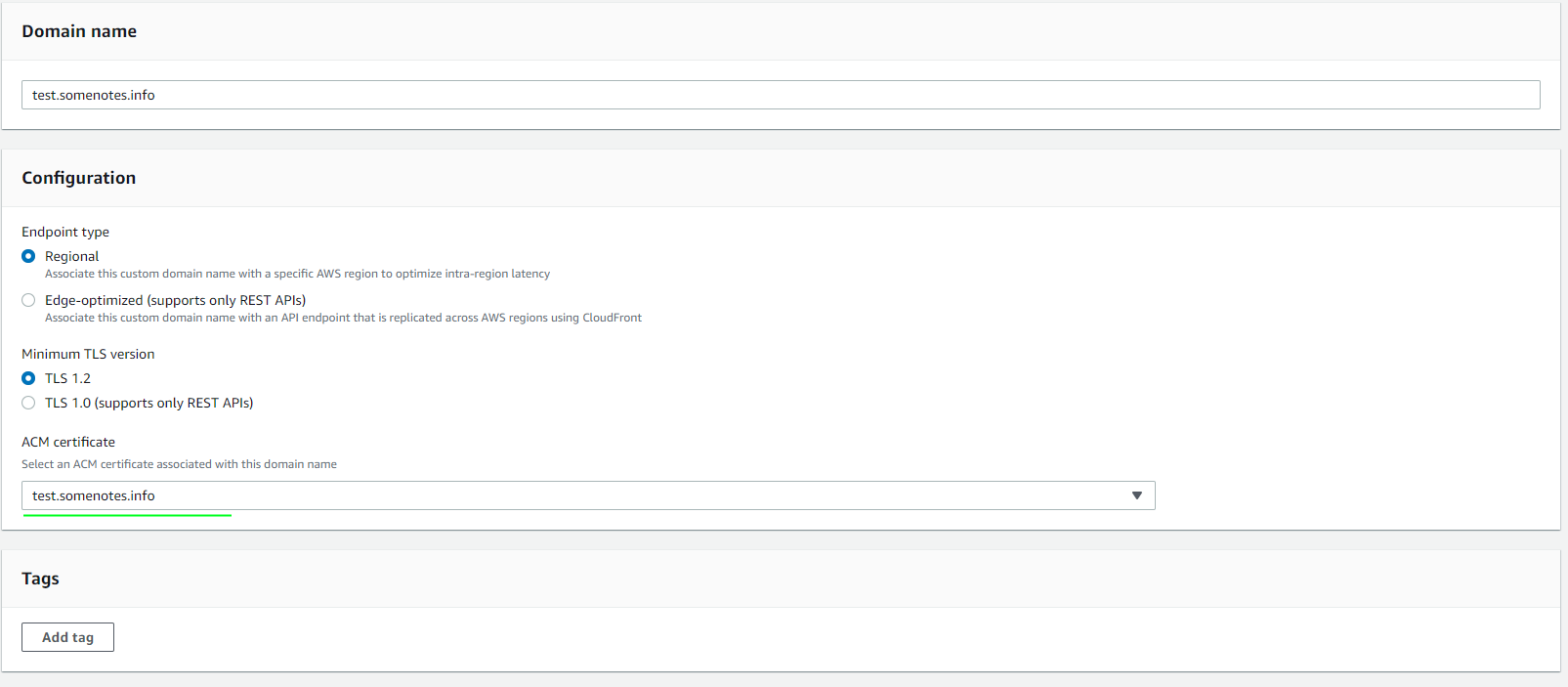
domainname:update API-call via the command line.
PATCH /domainnames/*Your API domain name*
Amazon CloudFront
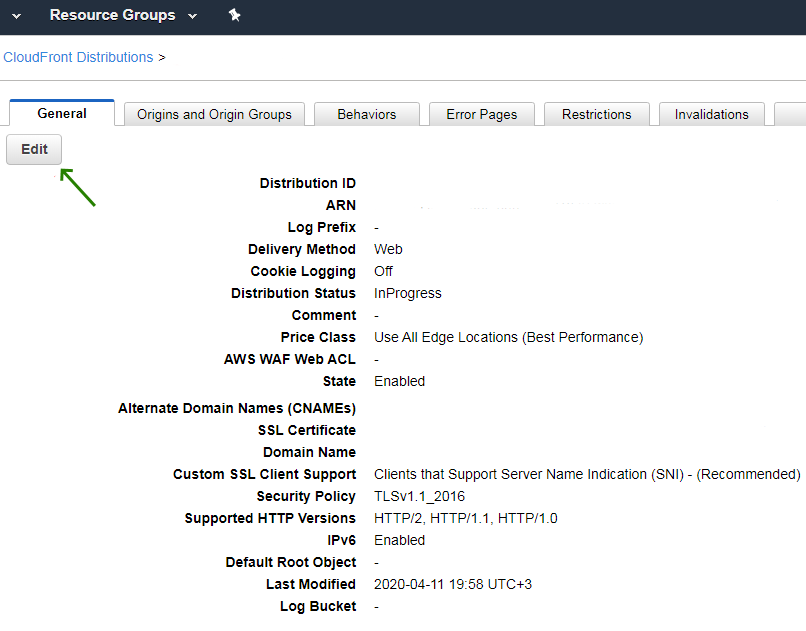
- Open your AWS console and go to the CloudFront console.
- Choose the ID of the CloudFront entity that needs to be updated.
- Go to the General tab and choose Edit.
- Update Alternate Domain Names (CNAMEs) with your SSL domain name(s) and choose the correct SSL from the list.
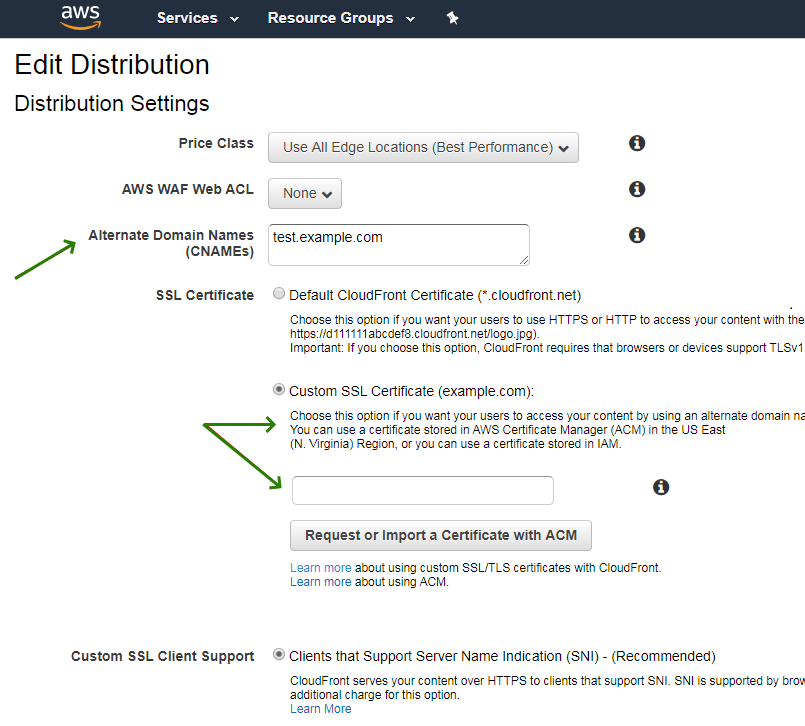
- Click Yes, Edit.
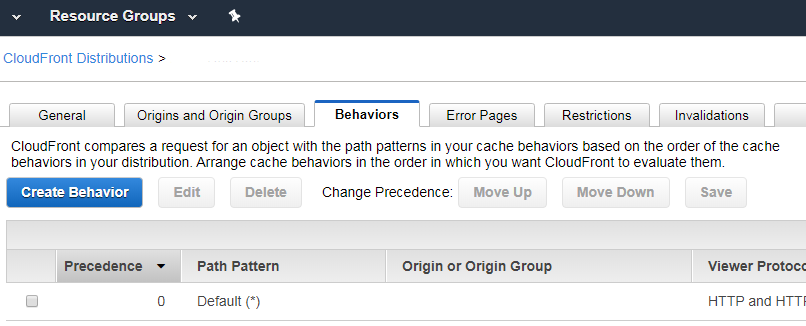
- After this, you can go to the Behaviors tab and either set a redirect from HTTP to HTTPS or set the Cloudfront to HTTPS only.
Categories
- cPanel Question 47
- cPanel Software Management 29
- cPanel Tutorials 13
- Development 29
- Domain 13
- General 19
- Linux Helpline (Easy Guide) 156
- Marketing 47
- MySQL Question 13
- News 2
- PHP Configuration 14
- SEO 4
- SEO 42
- Server Administration 84
- SSL Installation 54
- Tips and Tricks 24
- VPS 3
- Web Hosting 44
- Website Security 22
- WHM questions 13
- WordPress 148
Subscribe Now
10,000 successful online businessmen like to have our content directly delivered to their inbox. Subscribe to our newsletter!Archive Calendar
| Sat | Sun | Mon | Tue | Wed | Thu | Fri |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | ||||||
Recent Articles
-

Posted on : Sep 17
-

Posted on : Sep 10
-

Posted on : Aug 04
-

Posted on : Apr 01
Tags
- ts
- myisam
- vpn
- sql
- process
- kill
- tweak
- server load
- attack
- ddos mitigation
- Knowledge
- layer 7
- ddos
- webmail
- DMARC
- Development
- nginx
- seo vpn
- Hosting Security
- wireguard
- innodb
- exim
- smtp relay
- smtp
- VPS Hosting
- cpulimit
- Plesk
- Comparison
- cpu
- encryption
- WHM
- xampp
- sysstat
- optimize
- cheap vpn
- php-fpm
- mariadb
- apache
- Small Business
- Error
- Networking
- VPS
- SSD Hosting
- Link Building
- centos
- DNS
- optimization
- ubuntu